The following is a list of articles I have written. Below that is an overview of my scientific publications, which are all freely accessible on this website.
Writing
- ★ Advent of Code 2024, using Rust 2024
- What is PairSonic? 2024
- The Nexmon UDP Tunnel 2024
- Usability Evaluation of FIDO2 on Smartphones 2023
- Advent of Code 2022, using Clojure 2022
- ★ Advent of Code 2021, using J (jlang) 2021
- ★ Bring Your Own FIDO2 Extensions 2021
Publications
-
new!
Sounds Good? Fast and Secure Contact Exchange in Groups
Florentin Putz, Steffen Haesler, and Matthias Hollick
CSCW '24 27th ACM Conference on Computer-Supported Cooperative Work and Social ComputingAbstract
Trustworthy digital communication requires the secure exchange of contact information, but current approaches lack usability and scalability for larger groups of users. We evaluate the usability of two secure contact exchange systems: the current state of the art, SafeSlinger, and our newly designed protocol, PairSonic, which extends trust from physical encounters to spontaneous online communication. Our lab study (N=45) demonstrates PairSonic’s superior usability, automating the tedious verification tasks from previous approaches via an acoustic out-of-band channel. Although participants significantly preferred our system, minimizing user effort surprisingly decreased the perceived security for some users, who associated security with complexity. We discuss user perceptions of the different protocol components and identify remaining usability barriers for CSCW application scenarios.BibTeX
@inproceedings{cscw2024soundsgood, title = {Sounds Good? Fast and Secure Contact Exchange in Groups}, author = {Putz, Florentin and Haesler, Steffen and Hollick, Matthias}, publisher = {Association for Computing Machinery}, location = {New York, NY, USA}, year = {2024}, month = nov, booktitle = {Proceedings of the ACM on Human-Computer Interaction 8}, series = {CSCW2}, doi = {https://doi.org/10.1145/3686964} } -
new!
PairSonic: Helping Groups Securely Exchange Contact Information
Florentin Putz, Steffen Haesler, Thomas Völkl, Maximilian Gehring, Nils Rollshausen, and Matthias Hollick
CSCW '24 27th ACM Conference on Computer-Supported Cooperative Work and Social ComputingAbstract
Securely exchanging contact information is essential for establishing trustworthy communication channels that facilitate effective online collaboration. However, current methods are neither user-friendly nor scalable for large groups of users. In response, we introduce PairSonic, a novel group pairing protocol that extends trust from physical encounters to online communication. PairSonic simplifies the pairing process by automating the tedious verification tasks of previous methods through an acoustic out-of-band channel using smartphones’ built-in hardware. Our protocol not only facilitates connecting users for computer-supported collaboration, but also provides a more user-friendly and scalable solution to the authentication ceremonies currently used in end-to-end encrypted messengers like Signal or WhatsApp. PairSonic is available as open-source software: https://github.com/seemoo-lab/pairsonicBibTeX
@inproceedings{cscw2024pairsonic, title = {{PairSonic: Helping Groups Securely Exchange Contact Information}}, author = {Putz, Florentin and Haesler, Steffen and Völkl, Thomas and Gehring, Maximilian and Rollshausen, Nils and Hollick, Matthias}, publisher = {Association for Computing Machinery}, location = {New York, NY, USA}, year = {2024}, month = nov, booktitle = {Companion {{Publication}} of the 2024 {{Conference}} on {{Computer-Supported Cooperative Work}} \& {{Social Computing}}}, series = {{{CSCW}} '24 {{Companion}}}, doi = {https://doi.org/10.1145/3678884.3681818} } -
A Data-Driven Evaluation of the Current Security State of Android Devices
Ernst Leierzopf, René Mayrhofer, Michael Roland, Wolfgang Studier, Lawrence Dean, Martin Seiffert, Florentin Putz, Lucas Becker, Daniel R. Thomas
CNS '24 2024 IEEE Conference on Communications and Network Security (CNS)Abstract
Android’s fast-paced development cycles and the large number of devices from different manufacturers do not allow for an easy comparison between different devices’ security and privacy postures. Manufacturers each adapt and update their respective firmware images. Furthermore, images published on OEM websites do not necessarily match those installed in the field. Relevant software aspects do not remain static after initial device release, but need to be measured on real devices that receive these updates. There are various potential sources for collecting such attributes, including webscraping, crowdsourcing, and dedicated device farms. However, raw data alone is not helpful in making meaningful decisions on device security and privacy. We make a website available to access collected data. Our implementation focuses on reproducible requests and supports filtering by OEMs, devices, device models, and attributes. To improve usability, we further propose a security score grounded on the list of attributes. Based on input from Android experts, including a focus group and eight individuals, we have created a method that derives attribute weights from the importance of attributes for mitigating threats on the Android platform. We derive weights for general use cases and suggest possible examples for more specialized weights for groups of confidentiality/privacy-sensitive users and integrity-sensitive users. Since there is no one-size-fits-all setting for Android devices, our website provides the possibility to adapt all parameters of the calculated security score to individual needs.BibTeX
@inproceedings{cns2024datadriven, author={Leierzopf, Ernst and Mayrhofer, René and Roland, Michael and Studier, Wolfgang and Dean, Lawrence and Seiffert, Martin and Putz, Florentin and Becker, Lucas and Thomas, Daniel R.}, booktitle={2024 {{IEEE}} {{Conference}} on {{Communications}} and {{Network Security (CNS)}}}, title={A Data-Driven Evaluation of the Current Security State of Android Devices}, year={2024}, volume={}, number={}, pages={1-9}, doi={10.1109/CNS62487.2024.10735682}} } -
Introducing FreeSpeaker - A Modular Smart Home Hub Prototyping Platform
Hermann Leinweber*, Jonatan Crystall*, Frank Hessel, Florentin Putz, Matthias Hollick (* = equal contribution)
MobiCom '23 29th Annual International Conference on Mobile Computing and NetworkingAbstract
Smart home speakers have become a commodity item in many households and provide interesting research opportunities in areas like wireless communication and human-computer interaction. Commercial devices do not provide sufficient access for many research tasks. We present a modular smart home hub designed specifically for research purposes. The electronic and mechanical components are designed with reproducibility in mind and can be easily recombined for a project's needs. Additionally, we show applications of the hub in different scenarios.BibTeX
@article{mobicom2023freespeaker, title = {Introducing FreeSpeaker - A Modular Smart Home Hub Prototyping Platform}, location = {Madrid, Spain}, language = {en}, author = {Hermann Leinweber and Jonatan Crystall and Frank Hessel and Florentin Putz and Matthias Hollick}, eventdate = {02.-05.10.2023}, year = {2023}, month = {October}, doi = {https://doi.org/10.1145/3570361.3614080}, booktitle = {ACM MobiCom '23: Proceedings of the 29th Annual International Conference on Mobile Computing and Networking}, isbn = {978-1-4503-9990-6} } -
A Large-Scale Data Collection and Evaluation Framework for Android Device Security Attributes
Ernst Leierzopf, Michael Roland, René Mayrhofer, Florentin Putz
IDIMT '23 31st Interdisciplinary Information Management TalksAbstract
Android’s fast-lived development cycles and increasing amounts of manufacturers and device models make a comparison of relevant security attributes, in addition to the already difficult comparison of features, more challenging. Most smartphone reviews only consider offered features in their analysis. Smartphone manufacturers include their own software on top of the Android Open Source Project (AOSP) to improve user experience, to add their own pre-installed apps or apps from third-party sponsors, and to distinguish themselves from their competitors. These changes affect the security of smartphones. It is insufficient to validate device security state only based on measured data from real devices for a complete assessment. Promised major version releases, security updates, security update schedules of devices, and correct claims on security and privacy of pre-installed software are some aspects, which need statistically significant amounts of data to evaluate. Lack of software and security updates is a common reason for shorter lifespans of electronics, especially for smartphones. Validating the claims of manufacturers and publishing the results creates incentives towards more sustainable maintenance and longevity of smartphones. We present a novel scalable data collection and evaluation framework, which includes multiple sources of data like dedicated device farms, crowdsourcing, and webscraping. Our solution improves the comparability of devices based on their security attributes by providing measurements from real devices.BibTeX
@article{idimt2023large, title = {A Large-Scale Data Collection and Evaluation Framework for Android Device Security Attributes}, location = {Hradec Kr{\'a}lov{\'e}, Czech Republic}, language = {en}, author = {Ernst Leierzopf and Michael Roland and Ren{\'e} Mayrhofer and Florentin Putz}, eventdate = {06.-08.09.2023}, year = {2023}, month = {September}, doi = {https://doi.org/10.35011/IDIMT-2023-63}, booktitle = {IDIMT-2023: New Challenges for ICT and Management: 31st Interdisciplinary Information Management Talks}, isbn = {978-3-99151-176-2}, pages = {63--72} } -
DEMO: Secure Bootstrapping of Smart Speakers Using Acoustic Communication
Markus Scheck, Florentin Putz, Frank Hessel, Hermann Leinweber, Jonatan Crystall, Matthias Hollick
WiSec '23 16th ACM Conference on Security and Privacy in Wireless and Mobile NetworksAbstract
Smart speakers are highly privacy-sensitive devices: They are located in our homes and provide an Internet-enabled microphone, making them a prime target for attackers. The pairing between a client device and the speaker must be protected to prohibit adversaries from accessing the device. Most commercial protocols are vulnerable to nearby adversaries as they do not probe for human presence at the speaker or proximity between both devices. In addition to security, the protocol must provide a user-friendly way for initial bootstrapping of the speaker. We design an open pairing protocol for the establishment of a shared secret between both devices using acoustic messaging to guarantee proximity, and release our implementation for the smart speaker as well as Android and Linux clients as open-source software on GitHub.BibTeX
@article{wisec2023secure, title = {DEMO: Secure Bootstrapping of Smart Speakers Using Acoustic Communication}, language = {en}, author = {Scheck, Markus and Putz, Florentin and Hessel, Frank and Leinweber, Hermann and Crystall, Jonatan and Hollick, Matthias}, eventdate = {29.05. - 01.06.2023}, year = {2023}, location = {Guildford, Surrey, United Kingdom}, doi = {https://doi.org/10.26083/tuprints-00024180}, note = {Demo presented at the 16th ACM Conference on Security and Privacy in Wireless and Mobile Networks (WiSec 2023)} } -
FIDO2 the Rescue? Platform vs. Roaming Authentication on Smartphones
Leon Würsching*, Florentin Putz*, Steffen Haesler, Matthias Hollick (* = equal contribution)
CHI '23 ACM 2023 CHI Conference on Human Factors in Computing SystemsAbstract
Modern smartphones support FIDO2 passwordless authentication using either external security keys or internal biometric authentication, but it is unclear whether users appreciate and accept these new forms of web authentication for their own accounts. We present the first lab study (N=87) comparing platform and roaming authentication on smartphones, determining the practical strengths and weaknesses of FIDO2 as perceived by users in a mobile scenario. Most participants were willing to adopt passwordless authentication during our in-person user study, but closer analysis shows that participants prioritize usability, security, and availability differently depending on the account type. We identify remaining adoption barriers that prevent FIDO2 from succeeding password authentication, such as missing support for contemporary usage patterns, including account delegation and usage on multiple clients.BibTeX
@inproceedings{chi2023fido, title = {FIDO2 the Rescue? Platform vs. Roaming Authentication on Smartphones}, author = {W{\"u}rsching, Leon and Putz, Florentin and Haesler, Steffen and Hollick, Matthias}, publisher = {ACM}, location = {Hamburg, Germany}, eventdate = {23.-28.04.2023}, year = {2023}, isbn = {978-1-4503-9421-5}, month = {April}, booktitle = {CHI '23: Proceedings of the 2023 CHI Conference on Human Factors in Computing Systems}, doi = {https://doi.org/10.1145/3544548.3580993} } -
Future-Proof Web Authentication: Bring Your Own FIDO2 Extensions
Florentin Putz, Steffen Schön, Matthias Hollick
ETAA '21 4th International Workshop on Emerging Technologies for Authorization and AuthenticationAbstract
The FIDO2 standards for strong authentication on the Internet define an extension interface, which allows them to flexibly adapt to future use cases. The domain of establishing new FIDO2 extensions, however, is currently limited to web browser developers and members of the FIDO alliance. We show how researchers and developers can design and implement their own extensions for using FIDO2 as a well-established and secure foundation to demonstrate innovative authentication concepts or to support custom deployments. Our open-source implementation targets the full FIDO2 stack, such as the Chromium web browser and hardware tokens, to enable tailor-made authentication based on the power of the existing FIDO2 ecosystem. To give an overview of existing extensions, we survey all published FIDO2 extensions by manually inspecting the source code of major web browsers and authenticators. Their current design, however, hinders the implementation of custom extensions, and they only support a limited number of extensions out of the box. We discuss weaknesses of current implementations and identify the lack of extension pass-through as a major limitation in current FIDO2 clients.BibTeX
@inproceedings{putz2021futureproof, author = {Putz, Florentin and Sch\"{o}n, Steffen and Hollick, Matthias}, title = {Future-Proof Web Authentication: Bring Your Own {FIDO2} Extensions}, year = {2021}, isbn = {978-3-030-93746-1}, publisher = {Springer-Verlag}, address = {Berlin, Heidelberg}, url = {https://doi.org/10.1007/978-3-030-93747-8_2}, doi = {10.1007/978-3-030-93747-8_2}, pages = {17–32}, numpages = {16}, series = {ETAA '21} } -
Connected Self-Organized Citizens in Crises: An Interdisciplinary Resilience Concept for Neighborhoods
Steffen Haesler, Ragnark Mogk, Florentin Putz, Kevin T. Logan, Nadja Thiessen, Katharina Kleinschnitger, Lars Baumgärtner, Jan-Philipp Stroscher, Christian Reuter, Michele Knodt, Matthias Hollick
CSCW '21 24th ACM Conference on Computer-Supported Cooperative Work and Social Computing (Conference Companion Publication)Abstract
When facing major crisis events, such as earthquakes, flooding, or attacks on infrastructure, people start to organize within their neighborhoods. While this has historically been an analog process, people now use collaboration or messenger apps to support their self-organization. Unfortunately, these apps are not designed to be resilient and fail with communication infrastructure outages when servers are no longer available. We provide a resilience concept with requirements derived from an interdisciplinary view enabling citizens to communicate and collaborate in everyday life and during crisis events. Our human-centered prototype integrates concepts of nudging for crisis preparedness, decentralized and secure communication, participation, smart resource management, historical knowledge, and legal issues to help guide further research.BibTeX
@inproceedings{haesler2021connected, author = {Haesler, Steffen and Mogk, Ragnar and Putz, Florentin and Logan, Kevin T. and Thiessen, Nadja and Kleinschnitger, Katharina and Baumg\"{a}rtner, Lars and Stroscher, Jan-Philipp and Reuter, Christian and Knodt, Michele and Hollick, Matthias}, title = {Connected Self-Organized Citizens in Crises: An Interdisciplinary Resilience Concept for Neighborhoods}, year = {2021}, isbn = {9781450384797}, publisher = {Association for Computing Machinery}, address = {New York, NY, USA}, url = {https://doi.org/10.1145/3462204.3481749}, doi = {10.1145/3462204.3481749}, booktitle = {Companion Publication of the 2021 Conference on Computer Supported Cooperative Work and Social Computing}, pages = {62–66}, numpages = {5}, series = {CSCW '21} } -
Acoustic Integrity Codes: Secure Device Pairing Using Short-Range Acoustic Communication
Florentin Putz, Flor Álvarez, Jiska Classen
WiSec '20 13th ACM Conference on Security and Privacy in Wireless and Mobile NetworksAbstract
Secure Device Pairing (SDP) relies on an out-of-band channel to authenticate devices. This requires a common hardware interface, which limits the use of existing SDP systems. We propose to use short-range acoustic communication for the initial pairing. Audio hardware is commonly available on existing off-the-shelf devices and can be accessed from user space without requiring firmware or hardware modifications. We improve upon previous approaches by designing Acoustic Integrity Codes (AICs): a modulation scheme that provides message authentication on the acoustic physical layer. We analyze their security and demonstrate that we can defend against signal cancellation attacks by designing signals with low autocorrelation. Our system can detect overshadowing attacks using a ternary decision function with a threshold. In our evaluation of this SDP scheme's security and robustness, we achieve a bit error ratio below 0.1% for a net bit rate of 100 bps with a signal-to-noise ratio (SNR) of 14 dB. Using our open-source proof-of-concept implementation on Android smartphones, we demonstrate pairing between different smartphone models.BibTeX
@inproceedings{putz2020acoustic, author = {Putz, Florentin and \'{A}lvarez, Flor and Classen, Jiska}, title = {Acoustic Integrity Codes: Secure Device Pairing Using Short-Range Acoustic Communication}, year = {2020}, isbn = {9781450380065}, publisher = {Association for Computing Machinery}, address = {New York, NY, USA}, url = {https://doi.org/10.1145/3395351.3399420}, doi = {10.1145/3395351.3399420}, booktitle = {Proceedings of the 13th ACM Conference on Security and Privacy in Wireless and Mobile Networks}, pages = {31–41}, numpages = {11}, series = {WiSec '20} }
Authentication is the foundation for trustworthy communication over the Internet. I have worked on several projects evaluating and improving the deployability and usability of device pairing protocols as well as web authentication systems.
Usability is an often overlooked aspect of user-facing technology, especially in the security domain. But what good is such technology if users cannot successfully interact with it? Practical problems aren't just technological; they also demand solutions that are user-friendly and genuinely beneficial.
Teaching students was one of my tasks while working at TU Darmstadt. Besides the projects listed below, this website also contains an overview of my teaching activities.
I have been developing software for more than 15 years. This includes programming small tools, contributing to open-source software projects, but also building larger new software projects.
Major Projects
Setting up secure chats in messenger apps such as Signal is often a pain, as users have to manually verify the public keys of their contacts to ensure end-to-end encryption. Especially in larger groups, this process is cumbersome and can take a lot of time.
We have developed PairSonic, which is an open-source smartphone app that enables two or more users meeting in person to spontaneously exchange or verify their contact information. PairSonic simplifies the pairing process by automating the tedious verification tasks of previous methods through an acoustic out-of-band channel using smartphones’ built-in hardware. It does not rely on external key management infrastructure, prior associations, or shared secrets.
But is PairSonic really more user-friendly than current approaches? To answer this question, we conducted a user study where 45 participants compared PairSonic to the current state of the art. The questionnaires and subsequent interviews showed that participants significantly preferred our system PairSonic.
🏆 This study won a best paper award at CSCW’24 (top 1% of papers).
Passwords are the de-facto standard for user authentication, but they are hard to memorize and vulnerable to phishing/reuse attacks. Wouldn’t it be great if there was a standard way to use phishing-resistant public-key crypto for user authentication? Previous attempts suffered from poor usability, but FIDO2 and WebAuthn are promising.
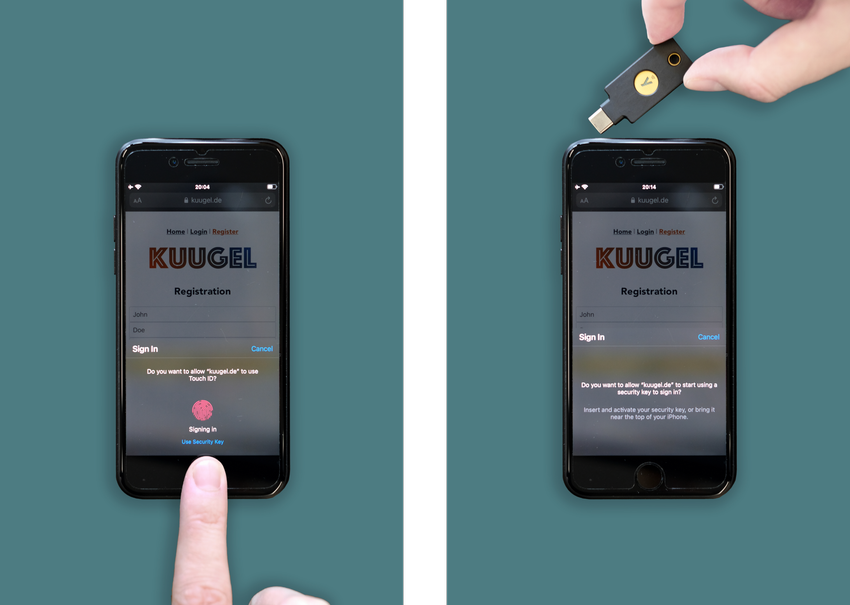
We analyzed the usability of FIDO2 passwordless authentication by conducting a lab study with 87 participants. We compared platform authentication (biometric) with roaming authentication (security key) to determine the practical tradeoffs as perceived by users in a mobile scenario.
🏆 This study won a best paper award at CHI’23, the top international conference for human-computer interaction.
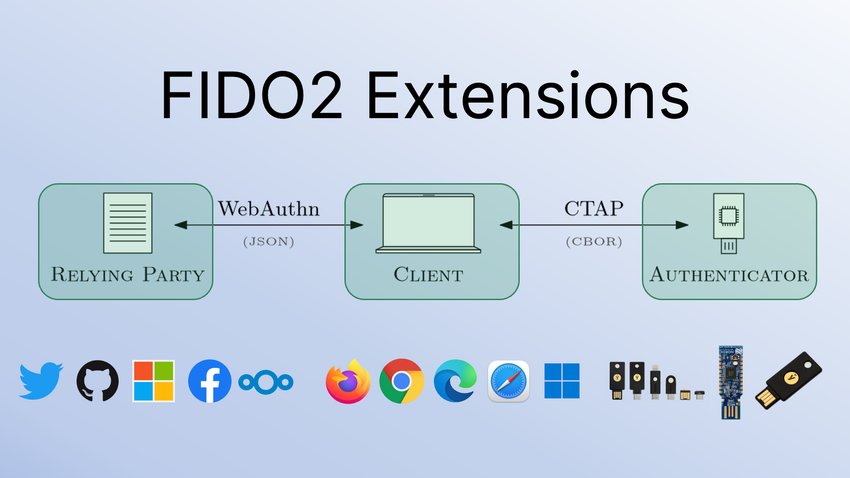
The FIDO2 standards for strong authentication on the Internet are now well-established in all major web browsers, allowing users to securely log in to websites without memorizing a password. But how can developers customize FIDO2 for their own use cases? Currently, there exists almost no information on custom FIDO2 deployments.
We documented the process of designing and implementing custom extensions for the FIDO2 web authentication protocol. Our open-source implementation targets the full FIDO2 stack, such as the Chromium web browser and hardware tokens. To give an overview of existing extensions, we survey all published FIDO2 extensions by manually inspecting the source code of major web browsers and authenticators. We propose methods to make it easier for developers to deploy custom FIDO2 extensions.
How can ordinary smartphones be used to securely exchange data with nearby devices? I designed a wireless physical layer that achieves message authentication using the acoustic interface, which is commonly available on smartphones and IoT devices. My open-source prototype implementation demonstrates device pairing with off-the-shelf smartphones and runs from user space without requiring firmware or hardware modifications.
🏆 This project started with my Master’s thesis, which has received two awards: The KuVS award 2020 (nationwide award for the best Master’s thesis on communication systems in Germany) and the Datenlotsen award 2020 (one of the best three STEM Master’s theses at TU Darmstadt).
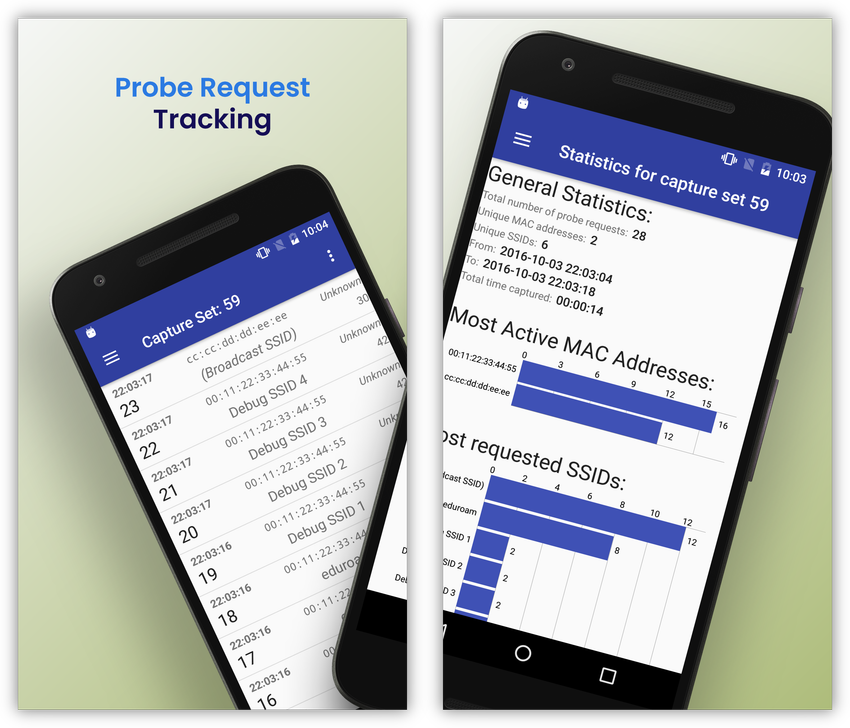
For my Bachelor’s thesis, I demonstrated a severe privacy vulnerability that affected most modern smartphones at the time, allowing for tracking and inferring location history of a user. I developed an Android app that can passively track wireless devices based on the WiFi probe requests they broadcast, showing tracking results in real-time.
The tracking data comes directly from the Broadcom WiFi chip, because I modified its firmware using the Nexmon reverse engineering framework (created by my thesis supervisor). Probe requests are special WiFi frames that are usually not accessible from user space. The tracking code therefore runs on a separate ARM chip instead of the host CPU, allowing continous tracking in the background without affecting normal smartphone usage and with minimal impact on battery usage.
Using this tracking system, I ran a measurement campaign to study the impact of this vulnerability by analyzing the probing behaviour of different smartphone models. Most devices were vulnerable and regularly sent probe requests, some even containing SSIDs of recently connected networks. As a response to such tracking approaches, Android and iOS nowadays randomize the MAC address to protect user privacy, but this was uncommon back when I evaluated this.
Minor Projects
The Advent of Code is an annual programming competition with fun problems for each day in December leading up to Christmas. Usually, I team up with some colleagues from work to participate, seeing each day who has the fastest or most creative solutions. I like to use this event as an opportunity to try out new programming languages.

My colleagues and I at SEEMOO designed a modular smart speaker that can be 3D printed (open-source electronic + mechanical components). We demonstrate practical device bootstrapping using an authentication protocol combining radio and acoustic signals.
The website you are visiting right now. I’m particularly proud of the responsive layout and responsive images. I did the web design from scratch, using the static site generator Jekyll with some custom plugins that I wrote in Ruby.
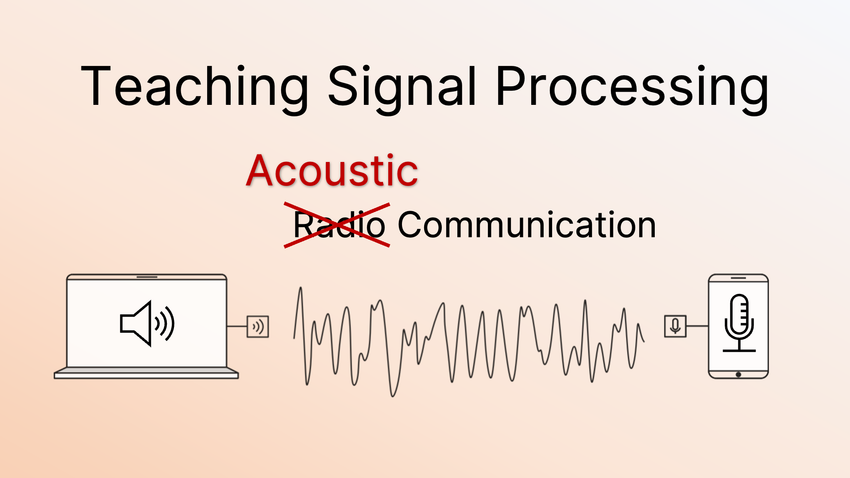
TU Darmstadt’s course on physical layer security includes many practical exercises where students come to our lab and experiment with radio signals using SDRs. During the COVID19 pandemic, this was no longer possible and we suddenly had to shift our course to an online offering.
It was still important for us to find a way to let students get hands-on experience (this is one of the main reasons students like the course), so I created a lab exercise which allowed students to experiment with the physical layer from home, entireley with their own hardware. Instead of radio signals, they generated acoustic signals which can be used to transmit and receive data using just their smartphones or laptops.
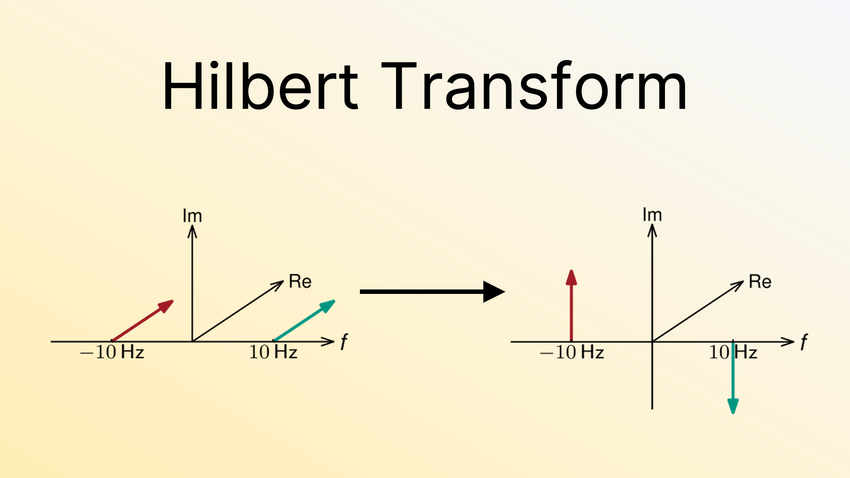
I created teaching material and a video tutorial to explain the Hilbert transform and how it relates to single-sideband modulation. In the past, our PhySec students particularly struggled with this topic. I’ve received great feedback: students claim that this tutorial helped them actually understand how it works and why it is useful in a visual way.
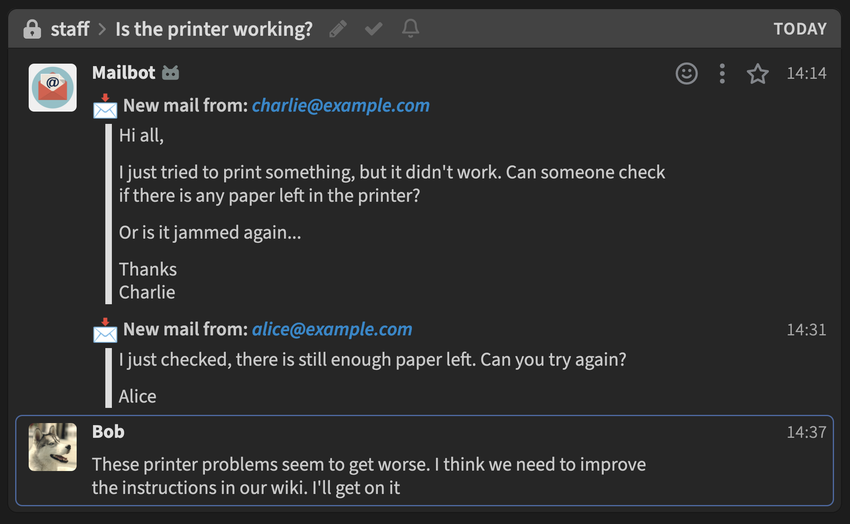
I have developed a bot that queries new mails from an IMAP server and mirrors them to a Zulip server. We used it back in the days at TU Darmstadt’s Computer Engineering student council to discuss incoming mails and coordinate actions/responses.